Over the weekend we were notified that our Windows DNS servers were being used in a "Open recursive resolver used for an attack". This is really a mistake on our part for putting the authoritative and recursive services on the internet facing systems, something we will have to change. Also because Windows DNS does not have ACL's like those that exist in Bind and PowerDNS etc, its not a simple case of adding the authorised ranges to the ACL allow recursion.
What I ended up doing was to write a couple of IPS rules to match requests with the DNS Query Flags of 0x0100. I also check for more than 5 requests per minute per source IP and when I get a match to both, I quarantine the source IP for a period of time. Since implementing this it has been working extremely well. I have only applied this rule to the rules pointing to our Windows DNS Servers and not our Linux DNS Servers.
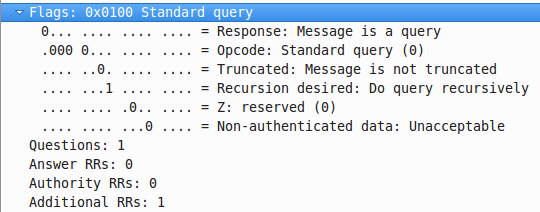
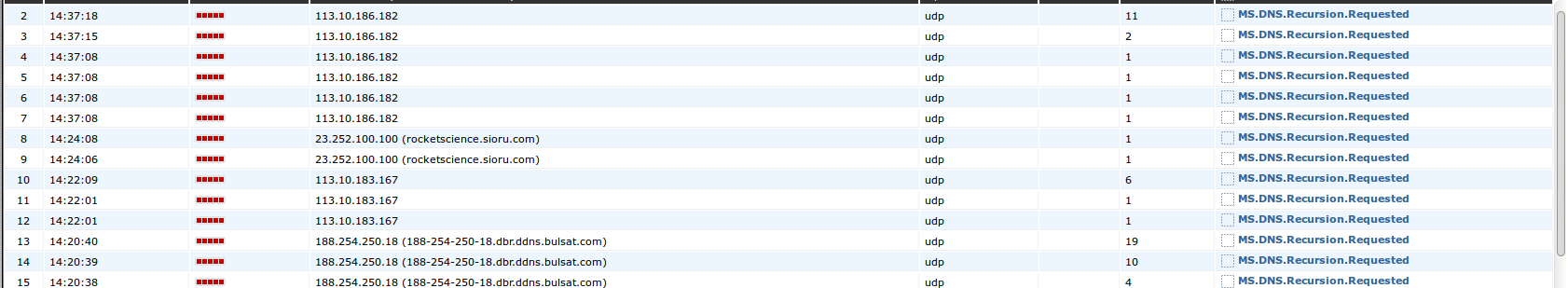
This is the flags of a recursive DNS query.
Here is how its done from the command line. Note this is on FortiOS Version 5.0 patch12
config ips custom
edit "MS.DNS.Recursion.Requested"
set action block
set comment ''
set severity info
set signature "F-SBID( --attack_id 8976; --name \"MS.DNS.Recursion.Requested\"; --ipver 4; --protocol udp; --service DNS; --pattern |0100|; --distance 2,packet; --flow from_client; --rate 5,60; --within 2,packet; --track src_ip; --log dns_query;)"
next
edit "MS.DNS.Recursion.Requested.V6"
set action block
set comment ''
set severity info
set signature "F-SBID( --attack_id 7731; --name \"MS.DNS.Recursion.Requested.V6\"; --ipver 6; --protocol udp; --service DNS; --pattern |0100|; --distance 2,packet; --flow from_client; --rate 5,60;--within 2,packet; --track src_ip; --log dns_query;)"
next
end
Now to add the IPS Sensor rule.
config ips sensor
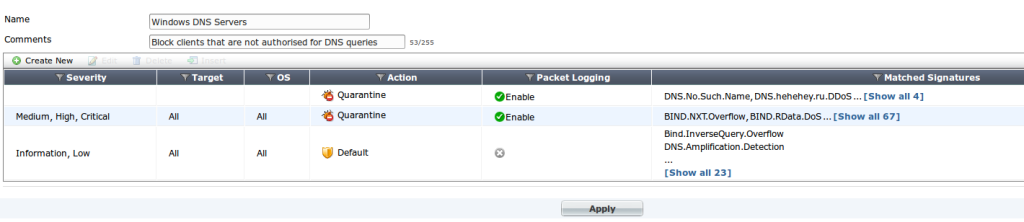
edit "Windows DNS Servers"
set comment "Block clients that are not authorised for DNS queries"
config entries
edit 4
set action block
set log-packet enable
set quarantine attacker
set quarantine-expiry 60
set rule 8976 7731
set status enable
next
edit 2
set action block
set log-packet enable
set protocol DNS
set quarantine attacker
set quarantine-expiry 30
set severity medium high critical
set status enable
next
edit 3
set protocol DNS
set severity info low
next
end
next
end
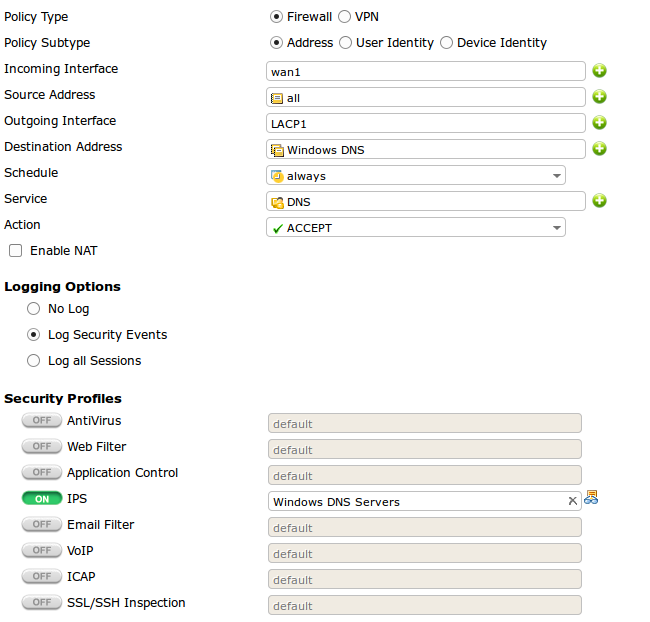
Finally the Firewall rule.
config firewall policy
edit 292
set srcintf "wan1"
set dstintf "LACP1"
set srcaddr "all"
set dstaddr "Windows DNS"
set action accept
set schedule "always"
set service "DNS"
set utm-status enable
set ips-sensor "Windows DNS Servers"
set profile-protocol-options "default"
next
end
This is the end result.